by nsiteamadmin | Jan 14, 2020 | 2020, AFRICA, All Publications, ASIA, Communications, EUROPE, Future Global Comp, Intent, MIDDLE EAST, NORTH AMERICA, Qualitative Analysis, SMA Publication, SME Elicitation, SOUTH AMERICA, Strategic Communication
Rethinking Communication Influence from a Strategic Communication Approach Authors | Editors: Lieber, P. (US Special Operations Command (USSOCOM) Joint Special Operations University (JSOU)); Canna, S. (NSI, Inc.) Executive Summary For over a decade, many within US...

by nsiteamadmin | Jan 10, 2020 | 2020, All Publications, Audio File, Bios, Briefing, DHS CAOE, MIDDLE EAST, Qualitative Analysis, SMA Speaker Series, SPEAKER SERIES, Terrorism
“Antecedents of Organizational Sophistication in Violent Non-State Actors in the USCENTCOM AOR” Speaker: Logan, M. (University of Nebraska, Omaha) Date: 10 January 2020 Speaker Session Preview SMA hosted a speaker...
by nsiteamadmin | Jan 2, 2020 | 2019, AFRICA, All Publications, ASIA, EUROPE, Geopolitics, MIDDLE EAST, NORTH AMERICA, Qualitative Analysis, SMA Publication, SOUTH AMERICA, Stability
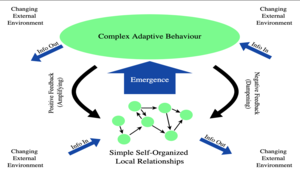
“Complex Adaptive Systems” Author | Editor: Lawson, S. (University of Utah); Canna, S. (NSI, Inc.) Executive Summary In his interview with Lt Col David Lyle (US Air Force Academy) on 4 June 2019, Dr. Sean Lawson discusses how complexity might inform...

by nsiteamadmin | Jan 2, 2020 | 2019, AFRICA, All Publications, Artificial Intelligence, ASIA, Australia, EUROPE, Future Global Comp, MIDDLE EAST, NORTH AMERICA, Qualitative Analysis, SMA Publication, SOUTH AMERICA
“Discrete, Specified, Assigned, and Bounded Problems: The Appropriate Areas for AI Contributions to National Security” Author | Editor: Rogers, Z. (Flinders University of South Australia); Canna, S. (NSI, Inc.) Executive Summary The cluster of technologies...

by nsiteamadmin | Dec 13, 2019 | 2019, All Publications, Audio File, Bios, Briefing, Cooley, S., DHS CAOE, Narrative Analysis, NORTH AMERICA, SMA Speaker Series, Social Media Analysis, SPEAKER SERIES, Text Analysis
“Contextualizing the Gray Rhino: The Central American ‘Cycle of Violence’ as a Catalyst to Migration” Speaker: Cooley, S. (Oklahoma State University) Date: 13 December 2019 Speaker Session Preview SMA hosted a speaker...

by nsiteamadmin | Dec 12, 2019 | 2019, AFRICA, All Publications, Artificial Intelligence, ASIA, Astorino-Courtois, A., Bragg, B., China, Economics, EUROPE, Future Global Comp, Geopolitics, Gray Zone, Hinck, R., Intent, MIDDLE EAST, Neuroscience, Peterson, N., SMA Publication, SME Elicitation, SOUTH AMERICA, White Paper, Wright, N.
“Chinese Strategic Intentions: A Deep Dive into China’s Worldwide Activities” Authors | Editors: Allen, G. (Center for a New American Security (CNAS)); Astorino-Courtois, A. (NSI, Inc.); Beckley, M. (Tufts University); Bragg, B. (NSI, Inc.);...








