
by nsiteamadmin | Dec 9, 2016 | 2016, All Publications, Canna, S., Communications, Edited Volume, Iraq, MIDDLE EAST, NORTH AMERICA, SMA Publication, SMA Reachback Cell, SME Elicitation, Strategic Communication, Syria, USA, ViTTa
Question (V1): What is Missing from Counter Messaging in the Information Domain. What are USCENTCOM and the global counter-ISIL coalition missing from countermessaging efforts in the information domain? Author | Editor: Canna, S. (NSI, Inc). “Western countries have...
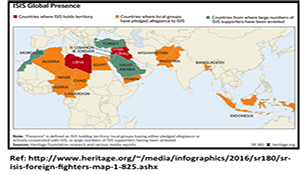
by nsiteamadmin | Dec 2, 2016 | 2016, All Publications, Communications, Edited Volume, Iraq, MIDDLE EAST, Qualitative Analysis, SMA Publication, SMA Reachback Cell, SME Elicitation, Spitaletta, J., Syria, Terrorism, ViTTa
Question (S3): What must the coalition do in the information environment to achieve its objectives in Iraq and Syria and how can it deny adversaries the ability to achieve theirs?Author | Editor: Spitaletta, J. (Johns Hopkins University Applied Physics Laboratory)....
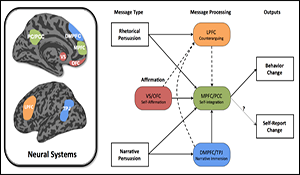
by nsiteamadmin | Oct 14, 2016 | 2016, All Publications, Communications, Edited Volume, Narrative Analysis, Neuroscience, SMA Publication, Social Network Analysis, Spitaletta, J., Terrorism
White Paper on Bio-Psycho-Social Applications to Cognitive Engagement. Author | Editor: Spitaletta, J. (Johns Hopkins University Applied Physics Laboratory). The recently released White Paper entitled “Assessing and Anticipating Threats to US Security Interests: A...
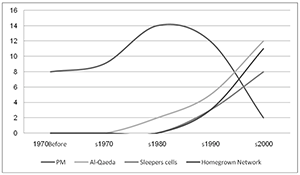
by nsiteamadmin | Jan 8, 2010 | 2010, Afghanistan, All Publications, ASIA, Communications, Computational Modeling, Edited Volume, EUROPE, Fenstermacher, L., Indonesia, Kuznar, L., MIDDLE EAST, Netherlands, Neuroscience, NORTH AMERICA, Pakistan, Predictive Modeling, Psychology, Qualitative Analysis, Rieger, T., Saudi Arabia, SMA Publication, Social Network Analysis, Speckhard, A., Statistical Analysis, Terrorism, United Kingdom, USA
Protecting the Homeland from International and Domestic Terrorism Threats: Current Multi-Disciplinary Perspectives on Root Causes, the Role of Ideology, and Programs for Counter-radicalization and Disengagement. Author | Editor: Fenstermacher, L. (Air Force Research...

by nsiteamadmin | Nov 3, 2006 | All Publications, Bayesian Modeling, Communications, Computational Modeling, Content Analysis, Decision Analysis, Game Theory, NSI Journal / Conf, Popp, R., Predictive Modeling, Quantitative Analysis, Simulation, Social Network Analysis, Statistical Analysis, Structured Argumentation, System Dynamics, Terrorism, Text Analysis
Countering Terrorism through Information and Privacy Protection Technologies Author: Popp, R. & Poindexter, J. Abstract Security and privacy aren’t dichotomous or conflicting concerns—the solution lies in developing and integrating advanced information...







